Setup and run Snort http://www.snort.org/ on the experimentation machines.
We start with the installation of snort.
sudo apt-get install snort sudo snort -dev -l ./snortlog
This also shows that snort works, what we have to do further with snort is that define a rule file, and attach it to the snort command with -c switch.
Next part is the simple statistic output from simple snort command above.
Snort received 48528 packets
Analyzed: 23527(48.481%)
Dropped: 23665(48.766%)
Outstanding: 1336(2.753%)
===============================================================================
Breakdown by protocol:
TCP: 17151 (72.899%)
UDP: 0 (0.000%)
ICMP: 0 (0.000%)
ARP: 0 (0.000%)
EAPOL: 0 (0.000%)
IPv6: 0 (0.000%)
ETHLOOP: 0 (0.000%)
IPX: 0 (0.000%)
FRAG: 0 (0.000%)
OTHER: 2 (0.009%)
DISCARD: 6374 (27.092%)
InvChkSum: 0 (0.000%)
===============================================================================
Action Stats:
ALERTS: 0
LOGGED: 23527
PASSED: 0
===============================================================================
Snort exiting
We wanted to have the nice webinterface, so we re-installed snort again the following tutorials:
-
- to install mysql_server, apache2, php5, snort-mysql and acidbase
- we used 145.100.105.32/27 as the home_net where snort should be listening on.
-
- for the oinkmaster installation with automatic rules update
- we needed to register on www.snort.org. to get the official rules.
Test if it's working.
In /etc/apache2/sites-available/default we added allow from 145.100.102.0/255.255.255.0 to be able to access snort from our workstations. Now browsing to http://145.100.104.16/acidbase/ we could see snort running.
Setup and run ntop http://www.ntop.org/on the experimentation machines.
Installing ntop was much easier than snort, just
- apt-get install ntop
- ntop -A (to set the Admin password)
- /etc/init.d/ntop start
Test if it's working.
Testing ntop just browse to http://145.100.104.16:3000/ and see ntop running
Configure a virtual machine that is running (pick one):
We choose:
- Windows 2003 SP0 server + MSSQL 2005 + IIS + ASP.
With the following command on our host machine, we can copy file to the windows 2003 server since it does not have internet connection. We have to download to our host first then manually copy the service pack and other files to it.
sudo mount -o loop,offset=32256 -t ntfs ./win2k3.img /mnt/windows/
We installed windows 2003 original. But we found to be able to install mssql2005 and the management tool, we need at least SP1 and windows installer v2. So we installed those. Then we can install sql2005 and management tool.
After the installation, we enabled iis and asp extension from control panel → add/remove software.
Make sure that the VMs are only accessible from the local network
We turned on windows firewall and only allowed IP range from the lab
no internet gateway!
Because of the firewall, nobody can access the system from outside, but we can use the internet outside.
Create a simple web application with the following characteristics and functionality:
Three files created:
- login.asp - this is the login page where user can put in user name and password
- welcome.asp - this is the landing page, on while user will see his salary or everybody's salary in case of an admin login
- functionsmyf.inc - this is the connection string to the database
<% Dim DBS, cst cst="Driver={SQL Server};" & _ "Server=OS3-YM8KLVOD4SQ\SQLEX;" & _ "Database=account;" & _ "Uid=test;" & _ "Pwd=test;" set dbs = CreateObject("ADODB.Connection") dbs.open cst %>
At least one database user account is created in the VM's database.
We create one database: account which has two tables: account and salary the account we used in the asp file is: test with password test.
Webpage input fields: username and password
user can input user name and password here. the login logic is also on this page.
<% If (name <> "" And password <> "") Then Set checkPwdTBL = Server.CreateObject("ADODB.RecordSet") checkPwdTBL.ActiveConnection = DBS checkPwdTBL.Open "SELECT account, password FROM account WHERE account = '" &name& "' AND password = '" &password& "' " If checkPwdTBL.EOF Then checkPwdTBL.Close Set checkPwdTBL = nothing response.write "Loginname or password is not correct. PLease try again." %> <SCRIPT LANGUAGE = "JavaScript"> <!-- message("Loginname or password is not correct. PLease try again."); //--> </SCRIPT> <% Else Session("Name") = name Session.LCID = 1033 Session.Timeout = "480" 'Timeout of session ID Set checkPwdTBL = nothing response.write "login OK" %> <SCRIPT LANGUAGE = "JavaScript"> <!-- window.location = "welcome.asp"; //--> </SCRIPT> <% End If End if %>
Webpage output:
User / pass correct: select database name and version from the database (use an SQL query to get this information from the database).
When the user name and password is correct, the welcome page will display the database name: account and the SQL version number. And the user's salary. In case the admin login, it will give all users' salaries.
User / pass incorrect: error message.
In case of failed login, an error message will be shown. But will not tell specifically if the user name is wrong or the password is wrong which weakens the strength of credentials.
Start a tcpdump on the base system: monitor the traffic to and from the VM.
- tcpdump tcp port 80 -i eth2 -s 0 -U -w /home/taarik/tcpdump.cap -n
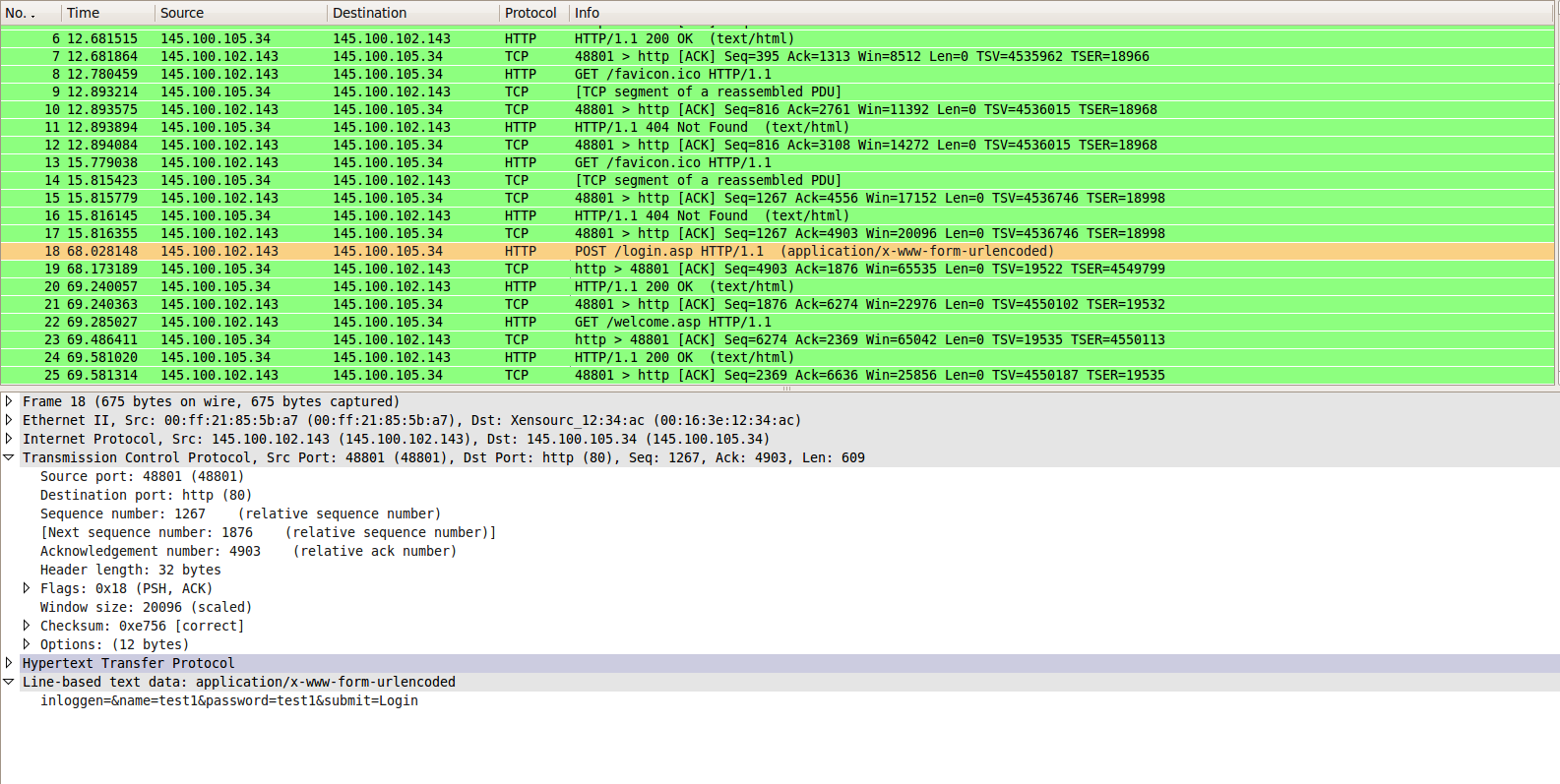
Logon to the web application you've created in the previous step. Do not use a browser that is running in the VM.
We browsed to the login interface on http://145.100.105.34/login.asp and logged in with the right credentials test1:test1
What do you see?
We can see the user:test1 password:test1 going over the line in plaintext, so it can be easily sniffed
How can you prevent this?
Just by using SSL you can encrypt this.
Install a SQL client package for the database system you're using and logon to the SQL server. Do not use the client package that is installed in the VM.
We installed the SQL manager from Eelco http://homepages.staff.os3.nl/~schatbrn/2009-2010/IDS/db/MSSQL 2005 Express/manager/SQLServer2005_SSMSEE.msi onto Vic's windows laptop to try and connect to the windows VM on meowth.
What do you see?
we now did a tcpdump on port 1433
- tcpdump tcp port 1433 -i eth2 -s 0 -U -w /home/taarik/tcpdump2.cap -n
Here we do not see any password, but see some other usefull information, like the servername, database + version used and the database name used to access the database.
How can you prevent this?
Use server certificates “ssl” to encrypt the communication channel in this case TCP port 1433
What did Snort detect?
We found snort detected something, but looking closer, we saw it was just the remote desktop we did to the vm, to configure the firewall. So snort did not do anything with this normal connection behaviour.
Does this cover all issues?
No, because snort is not configures to alert normal http and tcp connection. Except for those with high privileges, like RDP.
Can issues be solved by using encryption?
Yes ofcourse
Why / why not?
because when encrypted, eavesdropping becomes harder.